Yii2 is one of the popular PHP frameworks with difficult name to read. Correct use of frameworks significantly reduces development time, and also covers most of the security issues. But this, of course, does not mean the absolute safety of Yii2 applications, since there is always a human factor in any system. This short note shows a real case where code generation in Yii2 or any other framework can make problems with safety.
So, let’s say we have the “users” table:
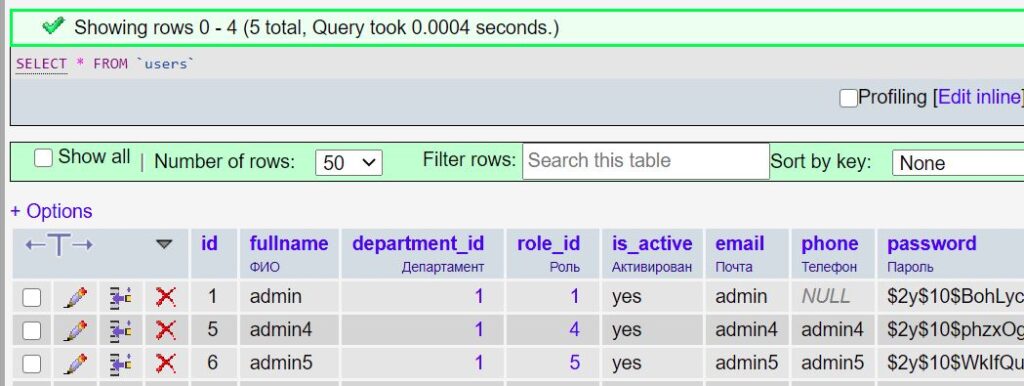
After generating a CRUD in Gii for the users table, we have a new UsersSearch.php file that is responsible for finding data in our table. From the entire file, we are interested in this piece of code:
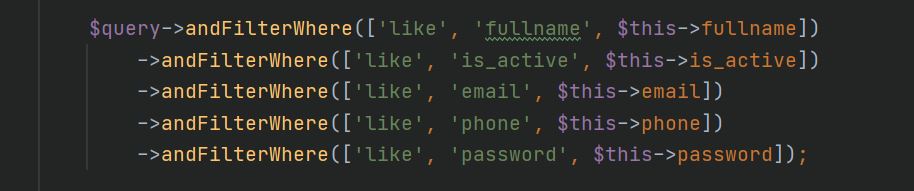
The soulless auto generation script, of course, doesn’t care whether users need to be searched by password, so it honestly generates a request for the “password” field. Often, developers remove the output of the password field from frontend part, but forget to remove it from the generated search class. As a result, you can do the following thing:
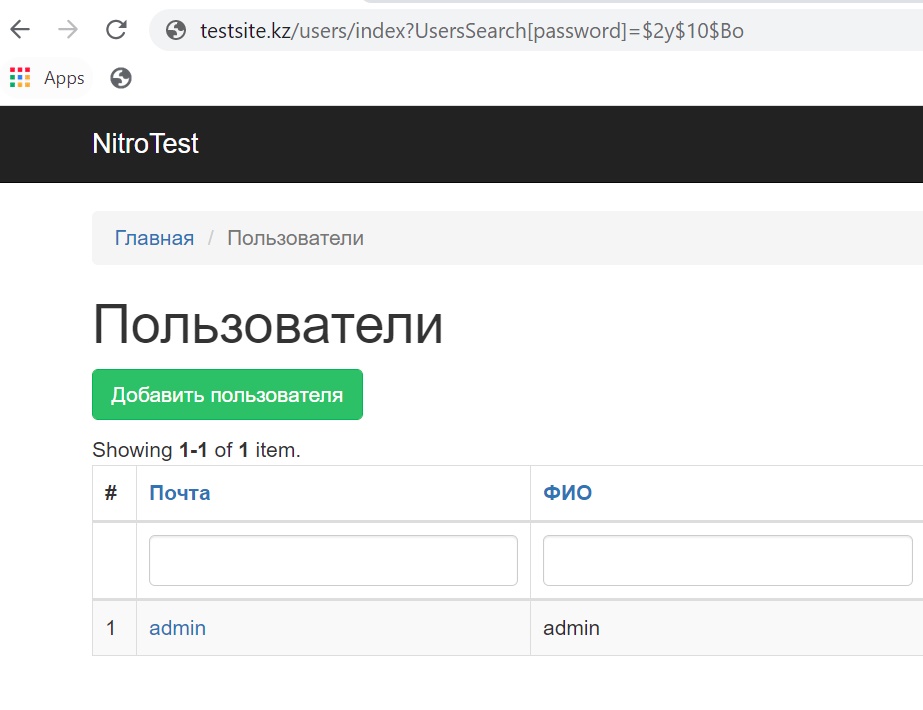
By adding the UsersSearch [password] parameter to the search query, we can guess the user’s password character by character. Although passwords are hashed with an irreversible function, you can always perform successful brute force the hash of a simple password. Even if it is not a password, it can be some kind of confidential information such as phone number, home address, etc.
For experienced developers we haven’t discovered something new, but we recommend to check your projects for the existence of such mistake. The information can be relevant for any frameworks that use similar code generation.